Secure Data Access at Scale
Every person and system that uses data is a potential attack vector. Minimize risk with centralized, consistent, control and visibility into who has access to sensitive data. By dynamically enforcing data access control policies, you will reduce your attack surface while leveraging your most important asset – your sensitive data.
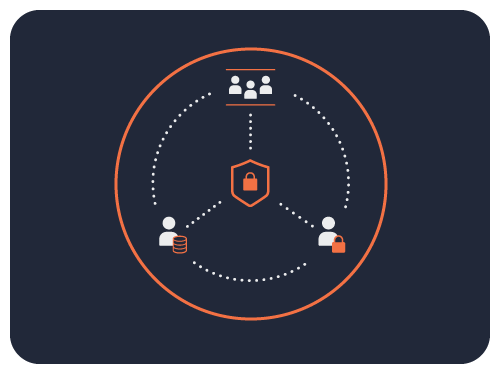
Supports Zero-trust Architecture for Modern Data Access Control
Data access control requirements aren’t what they used to be.
Managing access to massive amounts of confidential, personally identifiable (pii), and regulated data, distributed throughout multiple cloud and internal data platforms, requires new building blocks for success.
Turn off direct user access and delegate data authorization to Okera’s dynamic policy engine.
You can be confident that every query will be authorized based on the combination of the authenticated user’s roles, the target data attributes, and real-time query context.
Building Blocks Of Modern Secure Data Access
Authentication
Authenticate every query
Dynamic Authorization
On the fly policy enforcement
Sensitive Data Classification
Automated with APIs and ML
RBAC
Role-Based Access Control
ABAC
Attribute-Based Access Control
FGAC
Fine-grained Access Control
API-first Integrations
SQL DCL, Python, Java, and more
Distributed Stewardship
Assign authority and accountability
Data Usage Intelligence
Centralized auditing and reporting
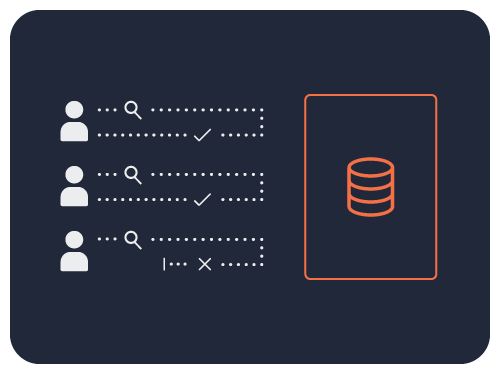
End-to-End Visibility and Data Usage Intelligence
Visibility is a significant part of data protection and is the foundation for proving compliance with internal mandates and government regulations.
Gain in-depth data intelligence through central authorization, logging, and auditing of user activity, data utilization, and policy changes.
Accelerate compliance reporting with full and granular visibility into who is accessing confidential, personally identifiable, and regulated data.
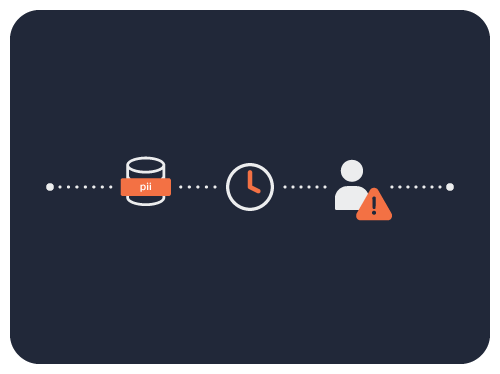
Identity-based Access and Authentication
Perimeter based security is too weak to protect data. Universal data authorization authenticates every data access request, and dynamically authorizes each query according to user role, data attribute, and even real-time query context
THREE SIMPLE STEPS TOWARD ZERO TRUST:
- Lock down the data at the source
- Continuously profile it for attributes that might be company confidential, PII, and regulated
- Authenticate every data request, then authorize for
Secure Data Access at Scale
Learn more, see it in action or try it yourself—>
