Audit and Analyze Sensitive Data Usage
Sensitive data usage intelligence for audit, security, and data privacy compliance teams.
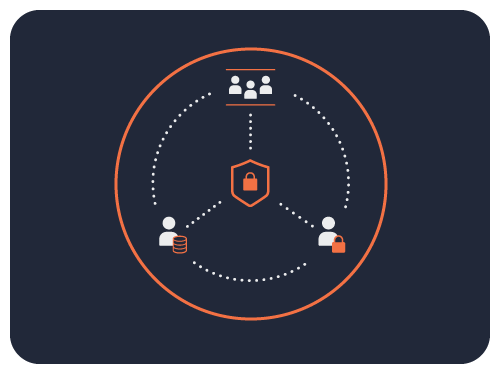
Sensitive Data Protection is Everyone’s Business
When it comes to managing sensitive data, there are a lot of stakeholders outside the data engineering team.
- Publicly traded companies have board-appointed financial audit committees, whose responsibilities include preventing insider trading
- The office of the CISO is generally responsible for making sure all corporate data is secured
- The Data Protection Officer is responsible for complying with the rapidly evolving landscape of data privacy regulations
- And more
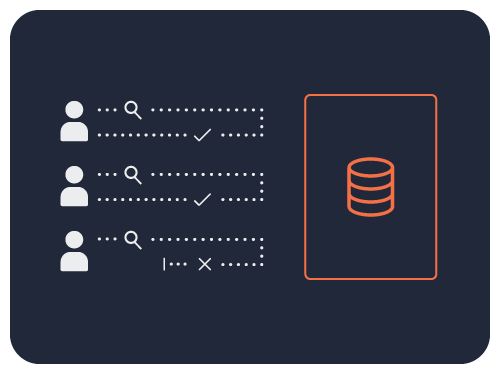
Self-Service Sensitive Data Usage Intelligence
Okera provides a collaborative platform that allows data stakeholders to get the info they need to perform their jobs.
Non-technical and authorized employees can see what sensitive data was accessed, when, how, and by whom.
- Identify and resolve data access violations more quickly
- Accelerate regulatory compliance reporting
- Monitor and respond more quickly to incidents
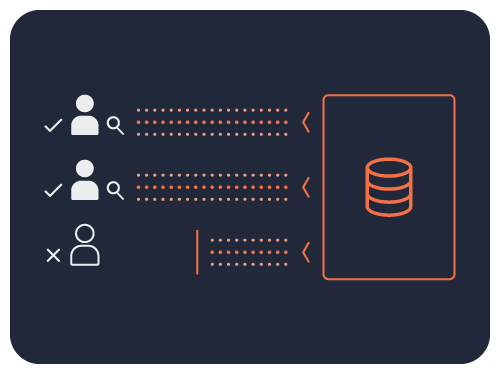
Okera Identifies Over-Provisioned Users
The principle of least-privilege is a key tenet of data security, data privacy, and regulatory compliance.
Okera can identify who isn’t using the data they’ve been granted access to. It’s the opposite of finding who has accessed sensitive data.
Instead, you’re looking to reduce risk.
Reducing the number of over-provisioned employees reduces the blast radius should a user’s credentials be compromised.
Show How Data Security Drives a Data-Driven Culture
It is hard to demonstrate whether a company has a data-driven culture. However, usage is a widely accepted metric. When data is trusted to be authoritative, more people use it more frequently.
As you protect more data with Okera, you can make it available to more users to use responsibly.
Rely on Okera’s built-in insights to demonstrate general usage trends over time as your company becomes more data-driven because they can use data responsibly.
Video: Audit User Activity and Understand Access
Learn how all data stakeholders can:
- Maintain least privilege access
- Audit and understand access to data
- Runtime: 00:04:02
Building and future-proofing your modern data analytics and data science stack
Learn how we integrate with market-leading, cloud technologies to enforce data security consistently across your modern architecture.