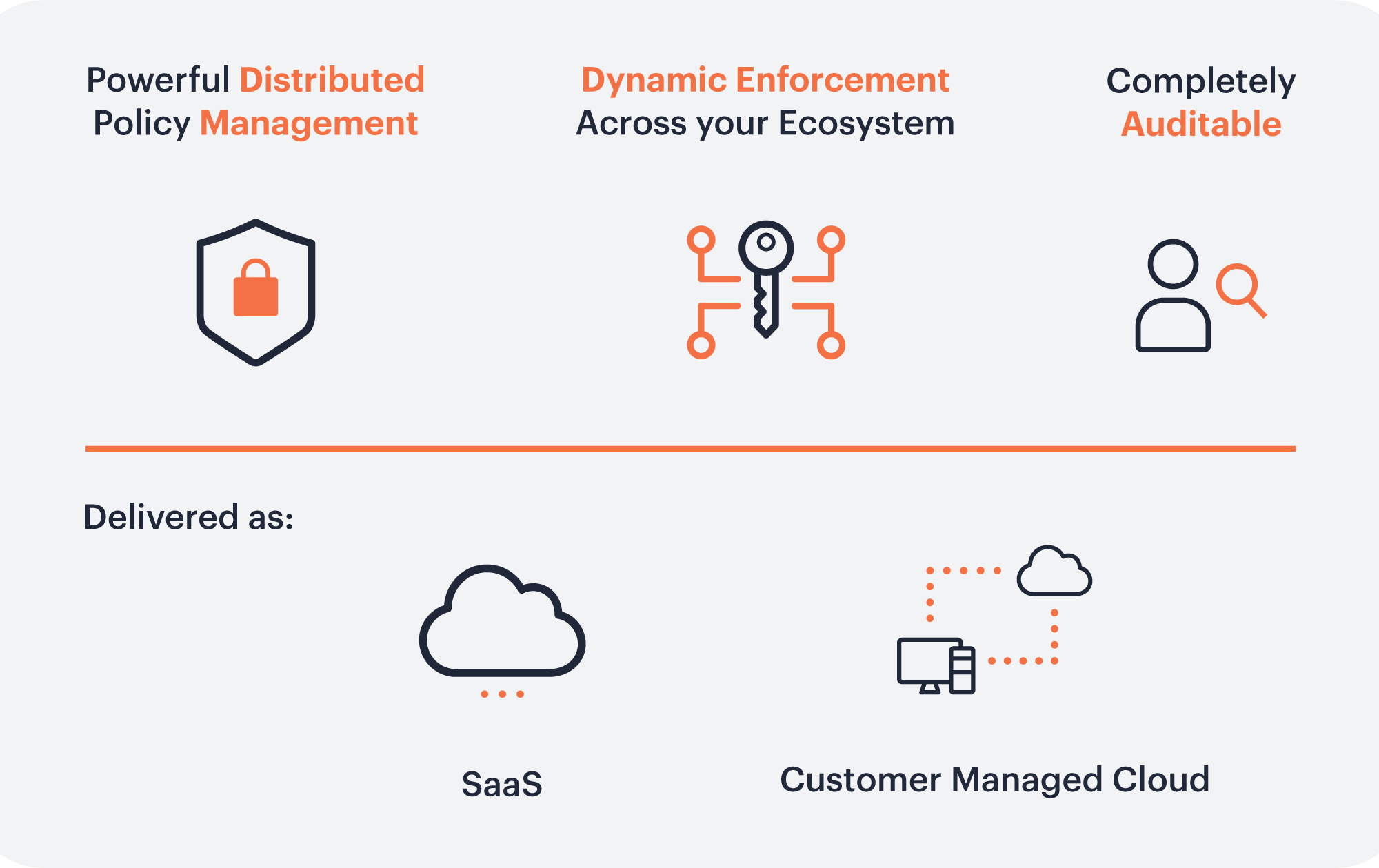
Dynamic Data Access Management
Okera speeds, simplifies, and secures data access starting with AI-centric data goverance
Data access policies need consistent enforcement
Whether building data products or a data mesh, technical teams need to balance their priorities with business value and impact across the organization.
Okera provides users with the confidence of treating data as an asset while protecting data at scale.
With Okera’s multiple enforcement patterns and platform-agnostic, policy-based data access control, policies are enforced consistently across all environments. It provides consistency, clarity, and economy of scale.
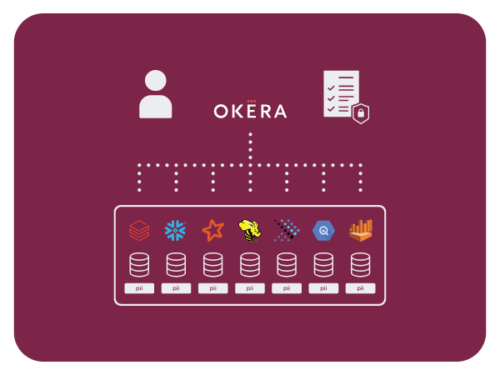
Discover & Classify Sensitive Data
“Knowing your data” is a prerequisite for achieving consistent, clear, and scalable data access governance.
Okera provides lightweight data discovery and classification capabilities, or you can configure Okera to integrate with your enterprise-grade data catalog. The choice is yours.

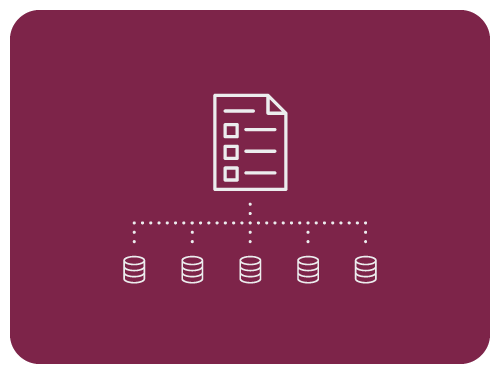
Collaborate and Manage Platform-Agnostic Data Policies
Okera abstracts policies into language that non-technical data stakeholders can understand. As a result, it’s easier for everyone to collaborate and agree on policies.
This means policies — and the data they protect — can be deployed faster and with greater confidence.
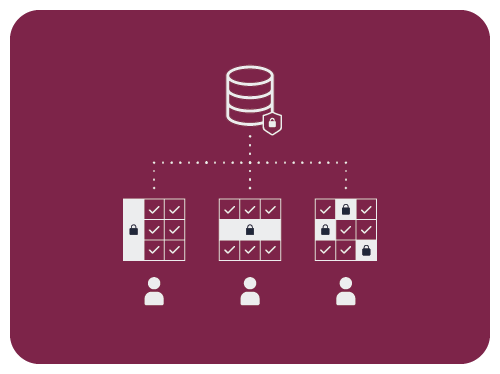
Dynamically Enforce Policies
Policies without enforcement are just words on a page.
Okera manages all the heavy lifting behind the scenes.
Multiple enforcement patterns make sure policies are enforced consistently across your cloud data warehouse, data lake, and data lakehouse.
Audit and Analyze Sensitive Data Usage
Audit, security, and compliance teams can use the Okera self-service portal to quickly find who requested sensitive data, when, with what application, and whether the request was denied or approved.
Learn how this frees up the data and IT teams to focus on their core work, accelerates compliance reporting, and can reduce incident response times.
Check out our library of resources
Learn about accelerating innovation while satisfying regulatory and security requirements.



