The world’s first AI-centric data governance platform.
Securing and liberating your data and AI models.
A New Chapter in Our Journey:
Okera is Joining the Databricks Family
Nong Li, CEO and co-founder of Okera, shares his journey and newfound excitement of joining Databricks to continue driving innovation in this exciting new age of AI. Read his story now.
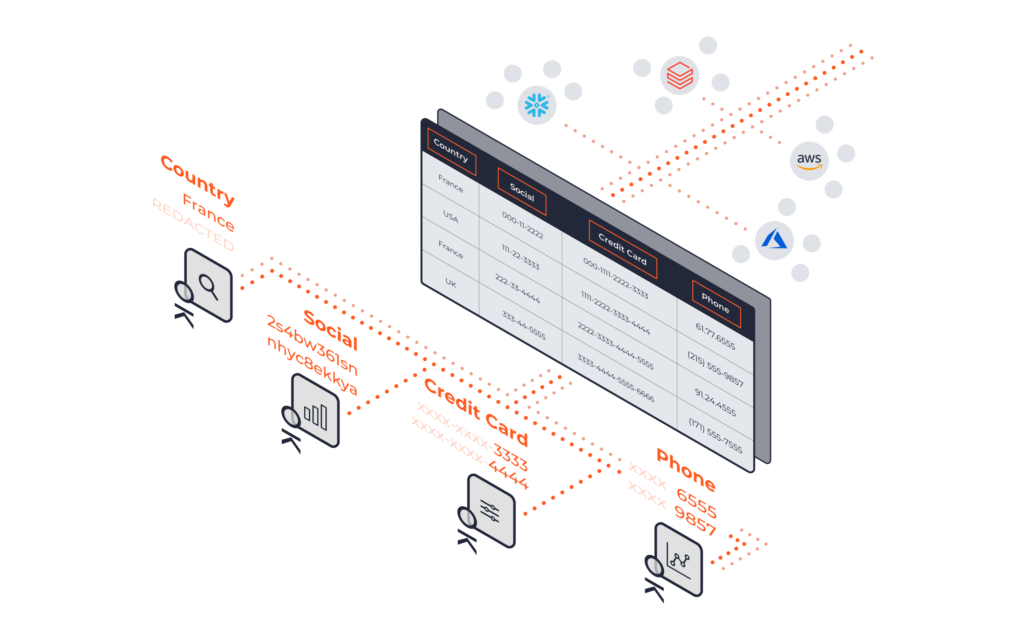
Speed innovation with AI-based data governance.
Do you recognize these blockers at your company?
The Can:
Over-provisioned and at-risk.
Analysts and data scientists can access sensitive data even when there's no legitimate business purpose.
The Cannot:
Locked-out and unaware of opportunities.
Business analysts cannot access data they need fast enough when co-mingled with sensitive data.
The Won't:
Stagnant and losing to market innovators.
Companies won't migrate sensitive data to the cloud, consumed by data security and privacy regulations.
If your analytics and data science practice isn’t delivering on expectations, don’t be discouraged!
Data security is the surprising secret to becoming data-driven and innovative.
Ensuring Secure Data Access Doesn't Have to Be Complicated
Industry leaders and practitioners agree that complexity is the enemy of security, and companies need to be able to understand the data they have and protect it from access by the wrong people. Hear top industry leaders weigh in on the challenges.
Centralize, simplify, and scale fine-grained data access control
Leverage all of your data to accelerate growth. Okera provides a common set of authorization policies applied in the same way, no matter where the data lives or how it is accessed. Use one policy to control data access across various data warehouses and lakes while authorizing attribute-based access control (ABAC) to files on an object store.
With our latest product release, OkeraEnsemble, users can now leverage policies with structured and unstructured data. This means:
- One single platform to analyze unstructured and structured data with all the data security and compliance included.
- Admins no longer need to create and manage complicated IAM policies.
- Users can dynamically enable access to only authorized users or groups to list, copy or view files.
- Data owners can elegantly define secure collaborative environments for analysts, data scientists, and low-code business users with read-and-write access.
Discover, Classify, and Secure Sensitive Data for AI
Okera offers cutting-edge technologies to address data governance challenges for companies operationalizing AI.

Discover and Tag Data with AI
Okera uses AI to automatically classify sensitive data. Columns can be tagged based on pattern matching or custom auto-tags can be created. Okera's new release now extends tagging and classification to files (images, documents, videos, and audio files).

Data Governance for AI
Self-service experience for data stewards to create and manage attribute-based and fine-grained data access control policies within one authoritative data set. Dynamically authorize user access to masked, tokenized, encrypted, or anonymized data.

Consistently Enforce Data Across Platforms
Enforcement patterns ensure policies are consistently enforced across your cloud data warehouse, data lake, and lakehouse platforms. Expanded ABAC principles to include files for better security and consistent policy enforcement using an easy to use GUI or Okera APIs.

Accelerate Regulatory Compliance Reporting
With self-serve data usage intelligence, non-technical, authorized employees can see who is accessing sensitive data, how and when - ensuring your AI use cases follow least privilege access principles.
We help companies provision, secure, and govern the world’s most sensitive data at scale.














Choose Your Journey.
The Okera platform is designed to support a variety of roles in the data value chain. Select your role below, to see how Okera can help you!
Data Leader
Your teams need data now to do their jobs. Some have data freely while others are completely blocked and neither serves the business appropriately.
IT Leader
Your organization recently moved or has plans to move to the cloud. Will your data be protected in the process?
Security Leader
“Zero access, that’s where you start.” This is what Jonathan Sander, Snowflake CTO said in an Airside keynote. “The whole exercise is to find a way to give access.”
Testimonials







