Introduction
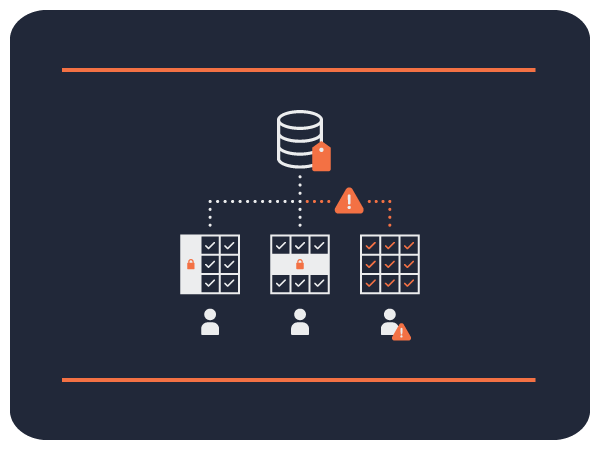
Fine-Grained Access Control (FGAC) is the pinnacle of data access controls: it’s the ability to obfuscate data at a row level, column level, and even down to a single cell on the execution of a query. How you achieve FGAC, however, is what separates organizations that can scale security with their data from those that cannot. Organizations around the globe strive for Fine-Grained Access Control, as it allows them to use more of their data and remain within the parameters of all regulatory and compliance rules.
What Is Fine-Grained Access Control?
Fine-grained access control is an approach to data access management that controls who can access what data.
Fine-grained control is not a new concept; it’s been around for quite some time. When FGAC was first introduced, teams were hard coding permission policies and writing long scripts in order to practice better data security and privacy hygiene.
While it can appear on the surface that this adds more complexity to your systems and slows progress down, it does not. Building in sound data security and access controls makes your systems easier to integrate, operate and scale.
Why is Fine-Grained Access Control Important?
What’s important here is that not only does FGAC shrink gaps in protecting PII(Personally Identifiable Information) /PHI(Protected Health Information)/Sensitive data, but it also allows companies to be responsible with their data. Opening more data to analysts, strategy, engineering, and product teams allows innovation to speed up.
On the contrary, if you leverage only coarse-grained access controls, whole datasets could be blocked from your teams due to PII/PHI/sensitive data in a given table. The major downside to this approach is that in that table existed other data that could provide value or insights into getting a 360-degree view of a product, consumer, or industry.
With fine-grained control, all your PII, PHI, and sensitive data can be leveraged to reduce gaps or errors in granting access to internal data sets that contain sensitive data. Now all data sets can be accessed across the company due to the fact that access policies can be written to exclude sensitive data. Now, that blocked data set can be opened and analyzed to give your team the full 360-degree view.
When Should FGAC Be Used?
FGAC should be implemented. If your organization has workflows of any of the following:
- The number of roles in your organization is unmanageable
- Company-wide innovation is slowing down
- Data in different geographic locations.
- Data that is subject to industry or government regulations.
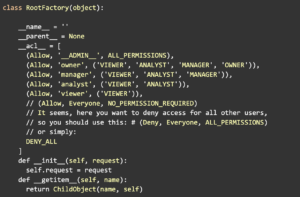
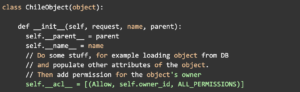
However, as environments changed and sensitive data became co-mingled with common data, along with the technological advancements which have allowed for cheaper computing and storage, we began to see exponential growth in the amount of data being stored. Hard coding policies are no longer an option as it’s not a scalable solution to sustain your security, privacy, compliance, and regulatory needs when we produce 2.5 quintillion bytes of data daily. Example scripts like the ones below can no longer be trusted in ensuring that all your data is being protected.
(the below code blocks are no longer sufficient as your company scales)
Imaging scaling permission like above out to hundreds and even thousands of employees. The scale of complexity leaves you vulnerable, and as the saying goes, “complexity is the enemy of security.” So what do you do?
Conclusion
We explored fine-grained access control and how it impacts data security, privacy, compliance, and regulatory needs, and we ultimately landed on how FGAC alone has hit a scaling problem. In our next post, we will examine how to truly scale fine-grained access control by leveraging role-based access control(RBAC) and attribute-based access control (ABAC).